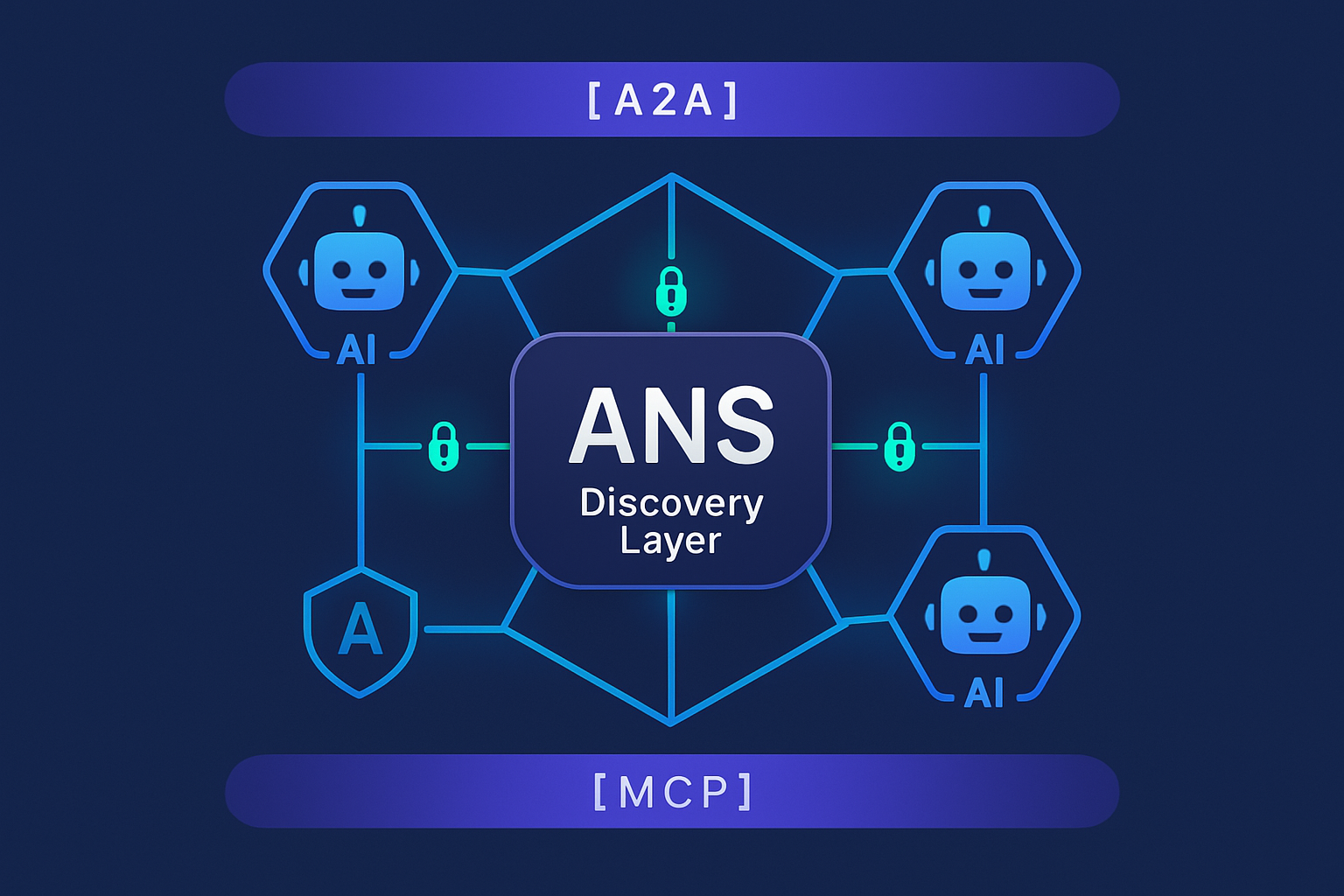
Introduction
I discovered the Agent Name Service (ANS) protocol entirely by chance. While exploring the implications of Anthropic’s Model Context Protocol (MCP) in late 2024, I stumbled upon a mention of ANS in a technical discussion thread. What started as mere curiosity turned out to be a remarkable find.
In the rapidly evolving ecosystem of autonomous artificial intelligence agents, secure discovery and interoperability between agents represent major challenges that MCP didn’t fully address. The Agent Name Service (ANS) protocol emerged as an unexpected piece of the puzzle, offering a robust mechanism for discovery, identification, and secure communication between AI agents.
Developed under the auspices of the OWASP GenAI Security Project and supported by major organizations such as AWS, Intuit, and Cisco, ANS represents a significant advancement in standardizing interactions between AI agents. This protocol, whose first official specifications were published in May 2025, draws inspiration from DNS while integrating modern security mechanisms adapted to the specific needs of autonomous agents.
What particularly surprised me about ANS was its ability to bridge the gap between different communication protocols like MCP and A2A, by providing this fundamental discovery layer that I wasn’t even looking for, but that was sorely missing from the AI agent ecosystem.
Problems Solved by ANS
The ANS protocol aims to solve several fundamental problems in AI agent ecosystems:
Human-unfriendly Identifiers
Similar to blockchain addresses that are difficult for humans to remember, AI agents often use complex identifiers that are not well-suited for human use. ANS provides a naming layer that maps human-readable names to secure agent identifiers [1, 2].
Lack of Standardized Discovery
Without ANS, AI agents from different providers struggle to discover and interact with each other, requiring custom integration for each agent interaction [3]. ANS establishes a common standard that facilitates this discovery.
Security Vulnerabilities
Current agent communication protocols, such as Anthropic’s Model Context Protocol (MCP) and Google’s Agent-to-Agent Protocol (A2A), lack protocol-specific security, making them vulnerable to various attacks such as agent impersonation, registry poisoning, and man-in-the-middle attacks [4, 5].
Centralized Control
Many existing naming systems rely on centralized authorities, creating single points of failure and censorship risks. ANS leverages decentralized approaches for greater resilience [6].
Comparison with Other Naming and Discovery Systems
I used the DeepResearch AI to create a comparative table for me. The idea is simply to understand with perspective where ANS stands in the table of discovered protocols.
General Comparison of Naming Systems
| System | Type | Decentralization | Security | Human-readable Names | AI Agent Specificity |
|---|---|---|---|---|---|
| ANS | Hybrid | ★★★★☆ | ★★★★★ | ★★★★☆ | ★★★★★ |
| DNS | Hierarchical | ★★☆☆☆ | ★★★☆☆ | ★★★★★ | ★☆☆☆☆ |
| Namecoin | Blockchain | ★★★★★ | ★★★★☆ | ★★★☆☆ | ★☆☆☆☆ |
| ENS (Ethereum Name Service) | Blockchain | ★★★★☆ | ★★★★☆ | ★★★★☆ | ★☆☆☆☆ |
| DIDs (W3C) | Decentralized | ★★★★★ | ★★★★★ | ★★☆☆☆ | ★★☆☆☆ |
ANS distinguishes itself by its specific design for AI agents, combining the advantages of existing systems while addressing the particular security and interoperability needs of autonomous agent ecosystems.
Detailed Comparison Between ANS, A2A, and MCP
To better understand the positioning and advantages of the Agent Name Service (ANS) protocol, it is essential to compare it with other major communication protocols for AI agents: Google’s Agent-to-Agent Protocol (A2A) and Anthropic’s Model Context Protocol (MCP).
Comparative Table
| Feature | ANS | A2A | MCP |
|---|---|---|---|
| Primary Purpose | Secure agent discovery and identification | Direct agent-to-agent communication | Integration of models with external tools |
| Primary Developer | OWASP GenAI / Consortium (AWS, Intuit, Cisco) | Anthropic | |
| Publication Date | May 2025 | April 2025 | November 2024 |
| Standardization Status | IETF Draft | Proprietary specification | Open specification |
| Identification Mechanism | PKI + DIDs | Proprietary identifiers | Contextual identifiers |
| Built-in Security | ★★★★★ | ★★★☆☆ | ★★☆☆☆ |
| Decentralization | ★★★★☆ | ★★☆☆☆ | ★☆☆☆☆ |
| Interoperability | ★★★★★ | ★★★☆☆ | ★★☆☆☆ |
| Extensibility | ★★★★☆ | ★★★★☆ | ★★★☆☆ |
| Maturity | Emerging | Emerging | Developing |
Comparative Analysis
Objectives and Scope
ANS primarily focuses on secure agent discovery and identification, serving as a foundational layer for the AI agent ecosystem. It provides a standardized mechanism for locating and authenticating agents before communication even begins.
A2A (Agent-to-Agent) is specifically designed for direct communication between agents, defining a standardized message format and exchange protocol. It focuses on how agents interact once they have discovered each other.
MCP (Model Context Protocol) is oriented toward integrating AI models with external tools and data sources. It defines how models can request and use external capabilities but doesn’t directly address agent discovery.
Architecture and Operation
ANS adopts a DNS-inspired architecture with a protocol adapter layer that allows it to integrate with A2A and MCP. It uses a hierarchical naming structure (ANSName) and relies on cryptographic mechanisms for security.
A2A defines a standardized JSON message format with specific fields for metadata, capabilities, and content. It includes mechanisms for session management and message routing but depends on other systems for initial discovery.
MCP uses a context model to enable AI models to interact with external tools. It defines how models can request actions, receive results, and maintain a conversational context, but doesn’t include robust mechanisms for authentication or discovery.
Security and Authentication
ANS integrates advanced security mechanisms from its design, using Public Key Infrastructure (PKI), Decentralized Identifiers (DIDs), digital signatures, and Zero-Knowledge Proofs (ZKP). It includes a comprehensive threat analysis based on the MAESTRO framework.
A2A includes basic security features such as message authentication but doesn’t offer the same level of built-in security as ANS. It often relies on external security layers for complete protection.
MCP primarily focuses on functionality rather than security, with limited mechanisms for authentication and protection against attacks. It is typically deployed in controlled environments where security is managed by other layers.
Complementarity and Integration
These three protocols are actually complementary rather than competitive:
- ANS provides the discovery and identification layer
- A2A offers a standardized protocol for agent-to-agent communication
- MCP enables the integration of models with external tools
ANS’s architecture recognizes this complementarity by including a protocol adapter layer that allows integration with A2A and MCP, thus creating a more coherent and interoperable ecosystem for AI agents.
Specific Use Cases
ANS excels in:
- Capability-based agent discovery
- Secure authentication between agents from different providers
- Resolution of human-readable names to technical identifiers
- Agent lifecycle management (registration, renewal, revocation)
A2A excels in:
- Direct and standardized communication between agents
- Defining consistent message formats
- Managing communication sessions
- Orchestrating multi-agent interactions
MCP excels in:
- Integrating AI models with external tools
- Managing conversational context
- Executing specific actions requested by models
- Returning formatted results to models
Conclusion on the Comparison
ANS, A2A, and MCP represent different layers of an emerging technology stack for AI agent ecosystems. ANS positions itself as the foundational layer for discovery and identification, while A2A and MCP focus on communication and integration aspects.
The future of AI agent ecosystems will likely depend on the seamless integration of these three protocols, each bringing its specific strengths to the whole. ANS, as the most recent development, fills a critical gap in this technology stack by providing the secure discovery layer that was previously missing.
ANS Protocol Architecture
The ANS protocol is structured around several interconnected components that work together to enable agent registration, discovery, and interaction.
Main Components
Registry Component: Acts as the central repository where agents register their capabilities, endpoints, and identifiers. This component maintains the mapping between human-readable names and cryptographic identifiers [7].
Discovery Mechanism: Enables agents to locate other agents based on capabilities or specific services needed. This component handles the querying and resolution of agent identifiers [8].
Communication Layer: Facilitates the actual interaction between agents once discovery is complete, supporting various interaction modes including text, audio/video, and structured data exchanges [8].
Security Layer: Ensures that all interactions are authenticated and authorized, preventing impersonation and unauthorized access to agent services. ANS integrates Public Key Infrastructure (PKI) for identity verification, digital signatures, and Zero-Knowledge Proofs (ZKP) for capability validation [9].
Extensibility Framework: Allows the protocol to be extended with new features while maintaining backward compatibility [10].
ANS Naming Structure
ANS defines a comprehensive naming structure (ANSName) that encodes protocol, agent capability, provider, and version metadata, enabling consistent and secure resolution across diverse agent networks [11]. This structure draws inspiration from DNS naming conventions while adding agent-specific features.
Protocol Adapter Layer
A major innovation of ANS is its modular protocol adapter layer that supports various communication standards:
- A2A Adapter: For integration with Google’s Agent-to-Agent protocol
- MCP Adapter: For integration with Anthropic’s Model Context Protocol
- ACP Adapter: For integration with the Agent Communication Protocol
This flexibility allows ANS to serve as an interoperability layer between different agent ecosystems [12].
Registration and Resolution Process
Agent Registration
The agent registration process in ANS typically follows these steps [13, 14]:
Initialization: The agent creates a unique identifier and generates cryptographic keys for authentication.
Registration Information Submission: The agent submits its registration details to the ANS registry, including:
- Agent identifier (typically a DID - Decentralized Identifier)
- Public key(s) for authentication
- Service endpoints
- Metadata about capabilities and services offered
Verification: The ANS registry verifies the agent’s credentials and ensures the uniqueness of the identifier.
Token Deposit/Staking: Depending on the implementation, agents may need to deposit tokens or provide a stake as part of registration [15].
Parameter Configuration: Agents set internal parameters including incentive distribution and service quality metrics [15].
Testing Period: New agents typically undergo a quality testing period (e.g., one week) before full activation [15].
Finalization: Upon successful verification and testing, the agent is registered in the ANS registry and becomes discoverable.
Resolution Process
When an agent needs to discover another agent, the resolution process occurs as follows [16, 17]:
Query Submission: The requesting agent submits a query with the target agent’s name or specific capability requirements.
Registry Lookup: The system searches the registry for the corresponding entry.
Resolver Processing: The resolver retrieves and processes the associated data.
Response Delivery: The system returns the resolved information (network address, public key, etc.) to the requesting agent.
Security Mechanisms
ANS integrates several advanced security mechanisms to protect the agent ecosystem [18]:
MAESTRO-Based Threat Analysis
The MAESTRO 7 Layers framework is used to identify and mitigate threats such as:
- Agent Impersonation: Countered by PKI-based authentication and digital signatures
- Registry Poisoning: Mitigated by consensus and verification mechanisms
- Man-in-the-Middle (MitM) Attacks: Prevented by encryption and mutual authentication
- Denial of Service (DoS/DDoS) Attacks: Limited by rate-limiting and staking mechanisms
PKI Security Controls
ANS heavily relies on Public Key Infrastructure for:
- PKI-based identity verification
- Digital signatures for message integrity
- Key rotation to maintain security over time
- Multi-signature schemes for enhanced security
Two-Way Authentication
The protocol implements two-way authentication between agents and servers using HTTP Message Signatures (RFC 9421) to ensure message integrity and authenticity [19].
Practical Use Cases
The ANS protocol enables numerous practical applications:
Secure Agent-to-Agent Collaboration
Specialized AI agents (e.g., a news scraper, summarizer, and distribution manager) can discover each other and collaborate securely [20]. This capability is particularly valuable in scenarios where multiple agents need to work together to accomplish complex tasks.
Cross-Platform Identity Management
Similar to how Clusters provides a unified identity layer across multiple blockchains, ANS can provide consistent agent identification across different platforms [21]. This allows agents to maintain a coherent identity regardless of the execution environment.
One-Click User Identification
ANS can facilitate secure user recognition through pre-established agent-to-agent connections, similar to how “Pico Agents” enable seamless authentication [22]. This feature significantly simplifies the user experience while maintaining a high level of security.
Middleware for Agent Discovery
Like Everyname’s approach to blockchain name resolution, ANS can serve as middleware that simplifies the discovery of agents across different ecosystems [23]. This abstraction layer reduces integration complexity for developers.
Implementation and Technical Considerations
TypeScript Implementation
The TypeScript implementation of ANS provides a robust foundation for developers to integrate this protocol into their applications, leveraging TypeScript’s strong typing system to ensure protocol compliance and security [24, 25].
Developers can model ANS protocol components using TypeScript interfaces and classes, with communication handled through standard web protocols like HTTP/HTTPS or WebSockets. Security features can be implemented using established cryptographic libraries and authentication mechanisms available in the TypeScript ecosystem.
Implementation Considerations
When implementing ANS, developers should consider several factors [26]:
- Scalability: Design to handle a large number of agents and resolutions
- Resilience: Mechanisms to handle failures and attacks
- Performance: Optimization for fast and efficient resolutions
- Interoperability: Support for various protocols and standards
- Governance: Mechanisms for protocol updates and evolution
Current Status and Future Prospects
The ANS protocol is a very recent development (May 2025), supported by major organizations and in the process of standardization at the IETF [27]. The first specifications have been published as an IETF draft and OWASP document, with increasing adoption expected in the coming months.
As the AI agent ecosystem continues to develop, ANS is positioned to become an essential standard facilitating interoperability and security in this rapidly evolving field.
Conclusion
The Agent Name Service (ANS) protocol represents a significant advancement in standardizing discovery and communication between AI agents. By combining DNS-inspired approaches with modern security mechanisms and a flexible architecture, ANS provides a robust solution to the challenges of identification, discovery, and interoperability in autonomous agent ecosystems.
The major innovation of ANS lies in its ability to bridge the gap between different agent communication protocols (A2A, MCP) by providing a secure discovery layer that was previously missing. Its modular design and security-oriented approach make it an essential piece of the emerging infrastructure for autonomous AI agents.
As we enter an era where AI agents play an increasingly important role in our digital systems, protocols like ANS will be essential to ensure that these agents can interact securely, efficiently, and in a standardized manner.
References
[1] OWASP GenAI Security Project, “Agent Name Service (ANS) for Secure Al Agent Discovery v1.0,” May 14, 2025. [Online]. Available: https://genai.owasp.org/resource/agent-name-service-ans-for-secure-al-agent-discovery-v1-0/
[2] K. Huang, V. S. Narajala, I. Habler, and A. Sheriff, “Agent Name Service (ANS): A Universal Directory for Secure AI Agent Discovery and Interoperability,” arXiv:2505.10609, May 15, 2025.
[3] K. Huang, V. S. Narajala, I. Habler, and A. Sheriff, “Agent Name Service (ANS): A Universal Directory for Secure AI Agent Discovery and Interoperability,” Internet-Draft, draft-narajala-ans-00, May 16, 2025.
[4] Anthropic, “Introducing the Model Context Protocol,” November 25, 2024. [Online]. Available: https://www.anthropic.com/news/model-context-protocol
[5] Google Developers Blog, “Announcing the Agent2Agent Protocol (A2A),” April 9, 2025.
[6] Solo.io, “Deep Dive MCP and A2A Attack Vectors for AI Agents,” May 5, 2025.
[7] W3C, “Decentralized Identifiers (DIDs) v1.0,” W3C Recommendation, July 19, 2022. [Online]. Available: https://www.w3.org/TR/did-core/
[8] Wikipedia, “Zooko’s triangle,” [Online]. Available: https://en.wikipedia.org/wiki/Zooko%27s_triangle
[9] IETF, “RFC 8949: Concise Binary Object Representation (CBOR),” December 2020. [Online]. Available: https://www.rfc-editor.org/rfc/rfc8949.html
[10] IETF, “RFC 9421: HTTP Message Signatures,” October 2024. [Online]. Available: https://www.rfc-editor.org/rfc/rfc9421.html
[11] A. Ehtesham et al., “A survey of agent interoperability protocols: Model Context Protocol (MCP), Agent Communication Protocol (ACP), and Agent-to-Agent (A2A),” arXiv:2505.02279, May 2025.
[12] Clarifai, “MCP (Model Context Protocol) vs A2A (Agent-to-Agent) Clearly Explained,” May 5, 2025.
[13] Dynatrace, “Agentic AI: How MCP and AI agents drive the latest automation revolution,” May 13, 2025.
[14] Akka.io, “MCP, A2A, ACP: What does it all mean?,” May 15, 2025.
[15] Gravitee.io, “Google’s Agent-to-Agent (A2A) and Anthropic’s Model Context Protocol (MCP),” April 18, 2025.
[16] The Register, “The Agent Name Service, it’s like DNS but for AI agents,” May 20, 2025.
[17] AIGL Blog, “Agent Name Service (ANS) for Secure Al Agent Discovery,” May 22, 2025.
[18] C. Greyling, “AI Agent Discoverability,” Medium, June 2025.
[19] Daily.dev, “DNS-Inspired Secure Discovery for AI Agents,” June 2025.
[20] LinkedIn, “Building a DNS-like Backbone for Autonomous AI Agents,” June 2025.
[21] Wikipedia, “Namecoin,” [Online]. Available: https://en.wikipedia.org/wiki/Namecoin
[22] Medium, “History of Namecoin: A Token Forked From Bitcoin’s Blockchain,” 2023.
[23] Blockchain-names.com, “Namecoin | Blockchain Naming Systems,” [Online].
[24] IETF, “RFC 1035: Domain Names - Implementation and Specification,” November 1987.
[25] IETF, “RFC 2782: A DNS RR for specifying the location of services (SRV),” February 2000.
[26] IETF, “RFC 8446: The Transport Layer Security (TLS) Protocol Version 1.3,” August 2018.
[27] Decentralized-intelligence.com, “Decentralized Naming and Zooko’s Trilemma,” June 11, 2023.